In the modern day and age of the internet, cybersecurity has emerged as an important discipline to safeguard people and companies against rising cyber attacks. For new entrants who wish to start their career as a cybersecurity engineer. There is plenty of information on the web, but well-organized books provide organized knowledge, detailed knowledge, and tested methods that are critical in laying solid foundations. We will also explore what cybersecurity engineer do?
Furthermore, whether you wish to learn ethical hacking, penetration testing, or malware analysis, these carefully curated cybersecurity books are just the place to start. They guide you from fundamental concepts to abstract approaches, which help you start your cybersecurity software engineer career with confidence.
How to Become a Cybersecurity Engineer?
A cybersecurity engineering career begins with a solid foundation in technology and progresses through real-world experience and ongoing learning. Here is an oversimplified primer to get you going:
1. Obtain the Proper Education
Start with a computer science, IT, or cybersecurity undergraduate degree. Study subjects such as networking, programming, cryptography, and operating systems to establish your technical foundation.
2. Acquire Practical Skills and Get Certified
Acquire skills such as scripting, threat hunting, and incident response. Industry-standard certifications such as CompTIA Security+, CISSP, or OSCP can increase your trust factor and job opportunities.
3. Get Hands-On Experience
Begin with junior or intern roles in IT or security. IT support or cybersecurity analyst positions allow you to apply what you have learned and gain hands-on experience.
4. Continue Learning
Cyber threats continue to evolve. Stay current with online education, bootcamps, webinars, and industry events. Building a portfolio through personal or open-source projects also makes you a better candidate.
5. Network and Find Opportunities
Participate in cybersecurity forums, go to events, and connect with professionals on sites like LinkedIn or groups like ISACA. Networking usually results in employment possibilities and priceless mentorship.
What is a Cybersecurity Engineer?
A cybersecurity engineer, or information security engineer, is a professional who is educated to plan, create, and put into practice security solutions to prevent networks, systems, and data from cyberattacks. Their role is to detect vulnerabilities, develop protective actions, and install devices to prevent cyberattacks. Cybersecurity engineers stay active in detecting possible security threats and having constant defense from unauthorized access, data breaches, and other cyber offenses. They contribute significantly to an organization’s security status by being proactive in regards to monitoring and developing security solutions.
What Does a Cybersecurity Engineer Do?
A cyber security engineer secures an organization’s information systems from cyber attacks. They set up and maintain security devices, watch for abnormal traffic, and react when attacked. Their work includes prevention, detection, and quick reaction to secure data and networks.
1. Designing Security Systems: Installing firewalls, IDS/IPS, and other devices to safeguard against attacks.
2. Identifying and Patching Vulnerabilities: Detecting system vulnerabilities and patching them prior to the bad guys exploiting them.
3. Responding to Incidents: Breaking down breaches, containing damage, and reconstituting secure operations.
4. Keeping Security Tools Up to Date: Updating systems to counter new threats.
5. Collaborating with IT Teams: Providing suggestions to developers and admins so that security is incorporated into every tech functionality.
6. Developing Security Policies: Writing rules of access for system and data to avoid misuse.
7. Pen Tests Conducting: Mimic attacks to expose hidden vulnerabilities.
8. Watching Network Activity: Pausing for abnormal action which can serve as a sign of an attack.
9. Eliminating New Threats: Attentive to new cyber threats to remain a step ahead of the attackers.
Also Read: What is IAM Engineer Salary in India in Different Countries in 2025
Qualifications Required to Be a Cybersecurity Engineer
To be a good cybersecurity data engineer, one requires education, technical knowledge, certifications, and real-world experience. Employers generally seek candidates who possess both theoretical and experiential knowledge of cybersecurity.
1. Educational Background
1. Bachelor’s Degree
The majority of cybersecurity engineers begin with a Bachelor’s Degree in Computer Science, Information Technology, Cybersecurity, or something similar. It gives your foundation in programming, networking, and security basics.
2. Master’s Degree (Optional)
Cybersecurity engineering masters degree or other technical discipline can enable you to specialize in areas such as cryptography, advanced threat detection, or security architecture keeping you ahead of the curve in senior positions.
2. Certifications
Certifications demonstrate to employers that you’re committed to your career and current with industry norms. Among the most coveted are:
- CISSP (Certified Information Systems Security Professional): The “gold standard” for senior security professionals.
- CompTIA Security+: A good place to begin that educates about basic security skills and knowledge.
- CEH (Certified Ethical Hacker): Pen testing and ethical hacking focus.
- CCNP Security: Network security advanced focus.
- CND (Certified Network Defender): Active network defense focus.
3. Technical Skills & Experience
Apart from degrees and certs, there are practical cybersecurity engineer skills. A cybersecurity engineer should be skilled in:
- Network protocols and architectures
- Security devices such as firewalls, IDS/IPS, and SIEM
- Programming or scripting languages such as Python or Bash
- Incident response and vulnerability management
What is Cybersecurity Engineer Salary?
Indian cybersecurity engineers’ salaries also vary based on experience, location, and employer. They receive an average salary of ₹3.0 Lakhs to ₹19.6 Lakhs, and senior executives receive better pay.
1. Freshers’ Salary
Freshers start at ₹3.0–₹6.0 LPA, precisely in positions such as cybersecurity analyst or junior security engineer.
2. Mid-Level to Experienced
At 3–5 years of experience, salary rises to ₹8.0–₹17.5 LPA. Additional specialized skill or qualifications can drive returns to the higher end of this range.
3. Senior Professionals
Gurus or veteran cybersecurity engineers receive ₹25 LPA and above. Data indicates the top 10% are paid more than ₹8.5 LPA, and the top 1% more than ₹12.1 LPA.
Pro Tip: Salaries vary by company and location; for example, at TCS, cybersecurity engineers earn between ₹2.2 and ₹10.4 lakhs per year.
Also Read: What is the Cyber Security Engineer Salary in India in 2025
What’s the Demand for Cybersecurity Engineers?
Cybersecurity engineers are in high demand and set to continue increasing as cyber attacks intensify and become more sophisticated. Businesses of all types are spending a lot on defending their networks and information, which is creating numerous opportunities for skilled staff.
1. Increasing Job Generation
Cybersecurity careers are estimated to increase by around 32% from 2022 to 2032, which is faster than the average rate of most jobs. Growth is attributed to increased cyber threats and more regulations.
2. Various Career Options
Cybersecurity has various career options such as Security Analyst, Ethical Hacker, SOC Analyst, Cloud Security Specialist, etc., where professionals can identify interests and abilities.
3. Lacking Talent
Even during the boom, a worldwide shortage of more than 3.5 million cybersecurity professionals exists, thus highly qualified engineers in demand.
4. Niche Specialities in Demand
Cloud security, IoT security, and advanced cryptography professionals are particularly well sought after as technology advances.
5. Exceptional Returns to Security
Due to the shortage of skills and mission-critical nature of their job, cybersecurity engineers possess the highest pay and excellent job security, thus making it even a good career choice.
What Requirements are There to Becoming a Cybersecurity Engineer?
There is a combination of education, experience, technical skills, certifications, and soft skills in becoming a successful cybersecurity engineer.
1. Education
A bachelor’s degree in IT, Computer Science, Cybersecurity, or any other related field is minimum required by most employers. A master’s degree is beneficial for unique or higher-level jobs.
2. Experience
Real-world experience is important. Internships, initial-level IT work, or volunteer experience in security projects develop skills involving firewalls, intrusion detection, endpoint security, and incident response.
3. Technical Skills
Knowledge of programming languages like Python, Java, and C++, knowledge of networking protocols (TCP/IP, DNS) and security tools (SSL, VPNs, encryption) is essential.
4. Certifications
CompTIA Security+, CISSP, and CEH certifications add credibility to your experience and exhibit your expertise to your employers.
5. Soft Skills
Effective communication, problem-solving, and analysis skills are required to communicate technical issues in plain language and work as part of a team.
6. Continuous Learning
Cybersecurity is constantly changing. Keeping up with new threats and technology is the secret to being sharp and current.
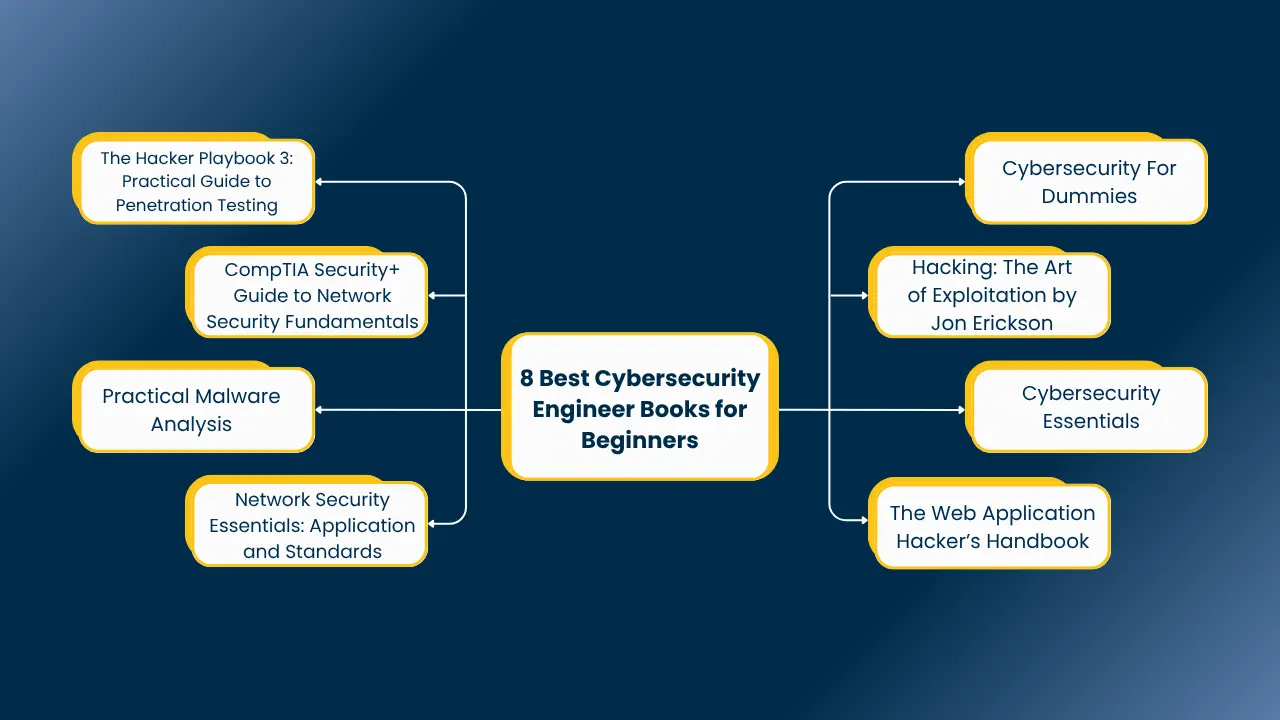
8 Best Cybersecurity Engineer Books for Beginners
If you’re just starting your journey into cybersecurity, having the right books can make a big difference. Whether you’re curious about ethical hacking or want to understand how cyber threats work, there are several beginner-friendly books that offer clear, engaging introductions to key concepts. Here are some highly recommended reads:
1. Cybersecurity For Dummies
Perfect for absolute beginners, this book explains essential cybersecurity concepts in a simple and accessible way. It’s a great place to start if you want a broad overview without getting overwhelmed.
2. Hacking: The Art of Exploitation by Jon Erickson
This classic goes deeper into the technical side of hacking. It shows how vulnerabilities are exploited, using examples and coding exercises to help you learn the hacker’s mindset.
3. Cybersecurity Essentials
A comprehensive guide to core cybersecurity principles, this book covers threats, vulnerabilities, and protection techniques ideal for building your foundational knowledge.
4. The Web Application Hacker’s Handbook
Focused on web application security, this book walks you through common vulnerabilities like SQL injection and cross-site scripting, and how to identify and prevent them.
5. Network Security Essentials: Applications and Standards
This one’s a solid introduction to network security, covering key protocols and standards, and how they apply in real-world cybersecurity defense.
6. Practical Malware Analysis
Want to understand how malicious software works? This hands-on guide teaches you how to dissect malware safely and understand its behavior.
7. CompTIA Security+ Guide to Network Security Fundamentals
If you’re preparing for the CompTIA Security+ certification, this book offers a clear roadmap. It covers key exam topics and real-world scenarios to help reinforce your learning.
8. The Hacker Playbook 3: Practical Guide to Penetration Testing
This book is all about applying your knowledge. It offers practical strategies and real-world examples for conducting penetration tests.
Read More: How to Become an IAM Engineer in India in 2025?
How Cybersec Trainings Can Help You Master in Cybersecurity Engineering?
Venturing into the industry of cybersecurity may be intimidating, more so for rookies. As lovely as studying through books and textbooks can become, systematic training and practical sessions will accelerate progress and boost confidence. That is where Cybersec Training takes charge.
We provide leading-edge training that not only discusses theoretical concepts but also scenario-based and hands-on skills to turn you into an effective ethical hacker or cybersecurity professional.
1. Hands-On Labs & Simulations
Practice hands-on penetration testing, malware analysis, and exploit development in safe, interactive labs real-world experience textbooks can’t deliver.
2. Expert Mentorship
Gain guidance from veteran cybersecurity professionals who discuss concepts, solve problems, and assist you in overcoming obstacles.
3. Current Curriculum
Stay updated on the latest attack techniques and defense strategies with the freshest course material, which is refreshed regularly.
4. Certification Preparation
Prepare for certifications such as CEH, CompTIA Security+, and others to pass exams with ease.
5. Career Guidance
Along with skills, resume building support, interview readiness, and placement assistance is provided to start or resume your cybersecurity career.
Conclusion
A career in cybersecurity engineer needs to be kicked off by knowledge as well as practice. These best cyber security and ethical hacking books are the learner’s best option, offering the basics of theories and practical approaches. But supplemented with practice and under the guidance of mentorship is required to be successful in the career. Through self-learning or conventional education, on-going learning is required to keep pace with changing cyber threats. Begin with these books as a reading recommendation to develop your skill set and then hone your expertise through hands-on training. With persistence and the appropriate tools, you can be an effective cybersecurity professional capable of addressing current challenges.