How to Become Identity Governance and Administration (IGA)?

In today’s digital high-speed lane, it’s more important than ever to track who has access to what within a business. That’s where Identity Governance and Administration (IGA) comes in. IGA helps organizations make sure the right people have the right access to the right systems and data nothing more, nothing less. This not only enhances security but also regulatory compliance.
With increased companies moving to cloud-based solutions and adopting advanced IT infrastructure, professional IGA experts are in greater demand. In this blog, we will discuss the key skills to succeed in this role, the certifications that can aid you in your growth, the career options waiting for you, and how Cybersec Trainings can help guide you to a meaningful career as an IGA professional.
What is an Identity Governance and Administrator?
An Identity Governance Administrator is an essential part of making an organization’s virtual world well-governed and secure. His or her main task is to guarantee that only the right people have access to the right systems and information and only when they need it. IGA Administrators manage user accounts, manage access rights, and implement security policies to help protect sensitive information.
Their role is quite critical in preventing unauthorized use and ensuring that the organization is compliant with regulatory demands. Aside from just coming up with policies, an Identity Governance and Administration makes them happen. What they do enables efficient operation, secures data better, and ensures the company remains compliant with standards across all departments and systems.
What Does an Identity Governance Administrator Do?
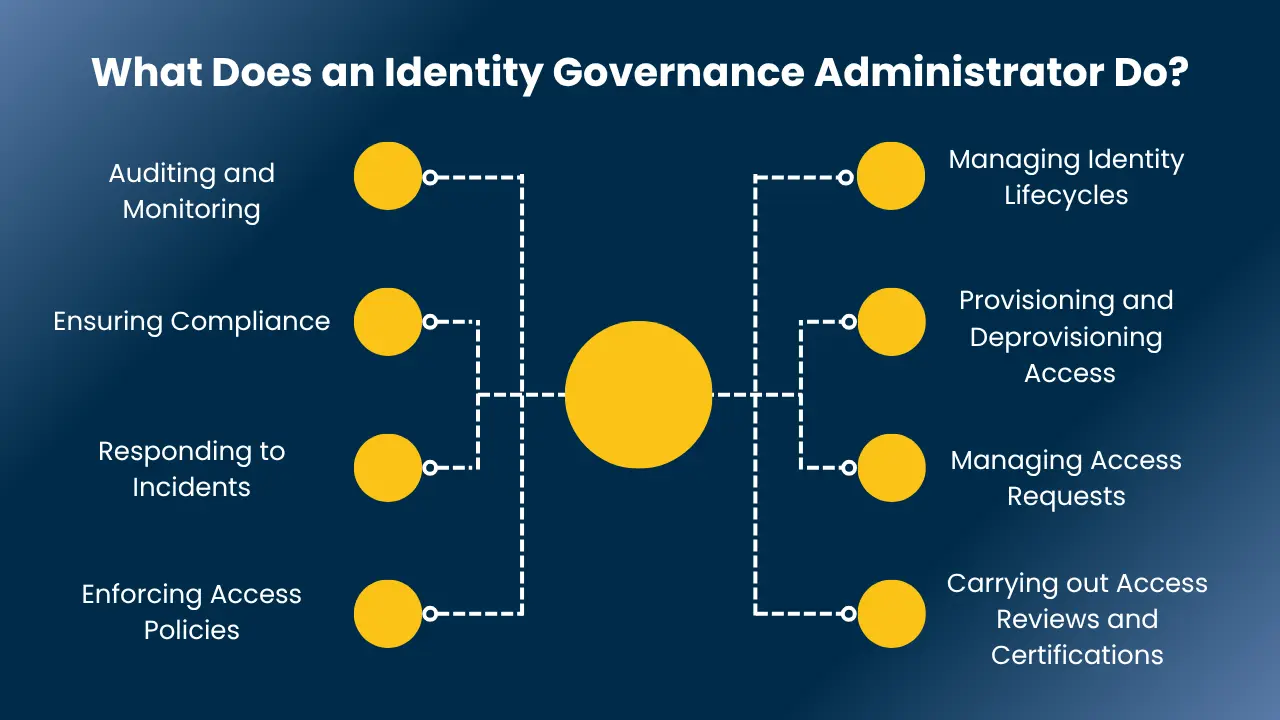
An Identity Governance Administrator has the significant responsibility of managing who accesses what in an organization keeping it secure, efficient, and compliant. Below are some of their main functions:
1. Managing Identity Lifecycles
They control the entire identity life cycle issuing accounts for new hires through to revoking access during role transition and offboarding departing employees securely.
2. Provisioning and Deprovisioning Access
Based on job role, they add or subtract access to information systems and data, in such a way that users have only what they need.
3. Managing Access Requests
They evaluate, authorize, or deny access requests, always according to company policies and security best practices.
4. Carrying out Access Reviews and Certifications
They regularly review whether users still need the access that has been granted, avoiding privilege creep and reducing risk.
5. Auditing and Monitoring
They track and analyze access behavior to detect policy non-compliance or suspicious activity that could be an indication of a threat.
6. Ensuring Compliance
They validate identity practices comply with laws like GDPR, HIPAA, and SOX, reducing the potential for legal issues.
7. Responding to Incidents
If something goes wrong such as unauthorized access they investigate, remediate the problem, and improve defenses.
8. Enforcing Access Policies
They apply and maintain consistent access rules across systems and departments to protect sensitive data and reduce insider threats.
Also Read: SailPoint IdentityIQ Training in Hyderabad: Fees, and Training Duration.
Educational Background and Prerequisites Required for Identity Governance and Administration
To become a successful Identity Governance Administrator, you’ll need the right mix of education, experience, and foundational knowledge in identity and access management.
Educational Background
Generally, employers require a bachelor’s degree in computer science, IT, cybersecurity, or related. This provides a strong background in networking, systems, and security fundamentals necessary for identity governance roles.
Professional Experience
Generally, you will require 3–5 years of experience with IAM, system administration, or security. This practical experience prepares you to handle identity lifecycle processes in actual scenarios and implement secure access across an organization.
Key Prerequisites
It is very important to build a strong foundation in core identity concepts, security practices, and having hands-on experience with relevant tools and cloud platforms. Therefore, we have mentioned the best 5 prerequisites that will help you to be well prepared in managing complex identity governance challenges.
1. Knowledge of Identity Concepts
You need to be aware of concepts like authentication, authorization, single sign-on (SSO), and identity flow in IT systems.
2. Knowledge of Security Best Practices
Security principles like least privilege, zero trust, and defense-in-depth are a requirement to deploy secure access controls.
3. Platform Experience
Hands-on experience with platforms such as Microsoft Azure or AWS is of great value especially in cloud-based environments.
4. Hands-On with Identity Governance and Administration Tools
Working experience of software such as SailPoint, Saviynt, or Oracle Identity Governance is usually required in current Identity Governance and Administration positions.
Essential Skills Required for Identity Governance and Administration
To be successful as an Identity Governance Administrator. You need a firm combination of technical and soft skills. Your job revolves around managing digital identities, enforcing access policies, and compliance precision, communication, and knowledge about Identity Governance and Administration tools are therefore extremely important.
Technical Skills
1. Identity Governance and Administration Platforms Proficiency
Practical experience in products like SailPoint, Saviynt, or Microsoft Entra ID Governance is crucial in managing access and enforcing security policies.
2. Database Management
You must be capable of handling identity information import, sync, and maintain integrity for reporting and audit purposes.
3. Integration Skills
Be familiar with REST APIs, LDAP, SOAP, and SCIM to integrate Identity Governance and Administration tools with HR systems, cloud applications, and other corporate software.
4. Programming & Scripting
Knowledge of Java, .NET, or PowerShell makes you capable of automating processes, customizing workflows, and integrating systems without hassles.
5. Access Administration
You need to be able to grant/revoke, manage authentication (e.g., SAML, OAuth), and conduct frequent access reviews.
6. Audit & Reporting
Access report generation, pattern analysis, and compliance audit support are essential to risk monitoring.
Soft Skills
1. Clear Communication
You need to describe access policy and user requests to IT teams and business users effectively. Access errors, system bugs, or policy conflicts? You’ll require razor-sharp troubleshooting skills to speedily get rid of them.
2. Attention to Detail
Even minimal access errors can create compliance problems so precision is not optional.
3. Organizational Skills
Managing user roles, systems, and deadlines means staying organized is absolutely essential.
4. Time Management
From audits to upgrades, being able to prioritize means that nothing falls through the cracks.
5. Adaptability
Technology and policy change quickly. Your adaptability keeps identity systems current and secure.
6. Risk Awareness
Awareness of risks like segregation of duties or unauthorized access enables you to recognize and fix issues before they are significant ones.
Also Read: What is the Identity Governance Administrator Salary in India in 2025
Top 6 Certifications Required for Identity Governance and Administration
If you wish to progress further in your career as an Identity Governance Administrator, certification is a good option. They not only recommend your skills but also enhance your credibility and result in more senior IAM and Identity Governance and Administration positions. Certifications such as Microsoft SC-300, CIAM, or CISSP may provide a competitive advantage and authenticate your proficiency.
1. Certified Identity Governance Expert (CIGE)
Ideal for senior professionals, this certification covers digital identity lifecycle, risk management, and governance strategy perfect for leadership or compliance professionals.
2. Certified Identity and Access Manager (CIAM)
Covers access risk assessment, compliance, and policy enforcement. Best for mid to senior-level IAM professionals.
3. Certified Identity Management Professional (CIMP)
A technical, practical certification for engineers and administrators who work directly with Identity Governance and Administration tools.
4. Microsoft Identity and Access Administrator Associate (SC-300)
Developed for IT professionals who manage Microsoft Entra ID (formerly Azure AD), this access-based certification delves into access control, identity lifecycle, and governance for hybrid/cloud environments.
5. Certified Access Management Specialist (CAMS)
Offered by the Identity Management Institute, it focuses on access controls, provisioning, and identity assurance.
6. Certified Information Privacy Manager (CIPM)
Complements your Identity Governance and Administration education with significant focus on managing privacy and regulations.
Job Opportunities and Career Paths for Identity Governance and Administration
As an Identity Governance and Administration (IGA) professional, you’ll find a wide range of job opportunities across the Identity Governance and Administration market. Whether you’re just starting out or looking to advance, there are roles like specialists, analysts, architects, and consultants. Many Identity Governance and Administration pros also transition into cybersecurity analyst positions or climb the ladder into leadership roles such as IGA Manager or Product Head.
Job Opportunities
1. IAM Specialist/Analyst
Concentrate on controlling user access, permissions, and enforcing security policies on a daily basis.
2. IAM Solutions Architect
Develop and deploy Identity Governance and Administration solutions that meet the needs of the organization.
3. Senior IAM Analyst
Perform system upkeep, perform access reviews, and enforce policy compliance.
4. IGA Implementation Consultant
Assist customers in implementing and operating their Identity Governance and Administration systems successfully.
5. Cybersecurity Analyst
Leverage your IGA knowledge to assist in more general cybersecurity efforts.
6. IGA Manager
Manage teams and projects, and guide the overall Identity Governance and Administration strategy.
7. Product Head Identity Governance and Administration
Guide vision and delivery of IAM products and services on a strategic basis.
Career Paths
1. Growth Within IAM
Move from analyst to specialist, and then to architect or management level.
2. Specialization
Go in-depth into specialized tools such as SailPoint or Saviynt, or specialize in areas like compliance or auditing.
3. Leadership
Assume team leadership, project management, or strategic roles influencing your organization’s IGA direction.
4. Consulting
Practice as a trusted advisor guiding companies to implement and optimize their IAM strategies.
5. Wider Cybersecurity
Broaden your career into broader cybersecurity roles that appreciate your IGA expertise.
Read More: How to Become a Sailpoint IdentityIQ Developer
Why to Pursue a Career as an Identity Governance and Administration (IGA) Professional?
An Identity Governance and Administration (IGA) career offers a great blend of technical know-how and business application. Identity Governance and Administration experts play a vital role in protecting firm information and systems and maintaining organizations compliant and streamlined. If you’re passionate about cybersecurity, puzzle-solving, and strategic teamwork with technology, IGA may be the rewarding career for you. Therefore, we have mentioned the best reasons for identity governance and administration to be your career.
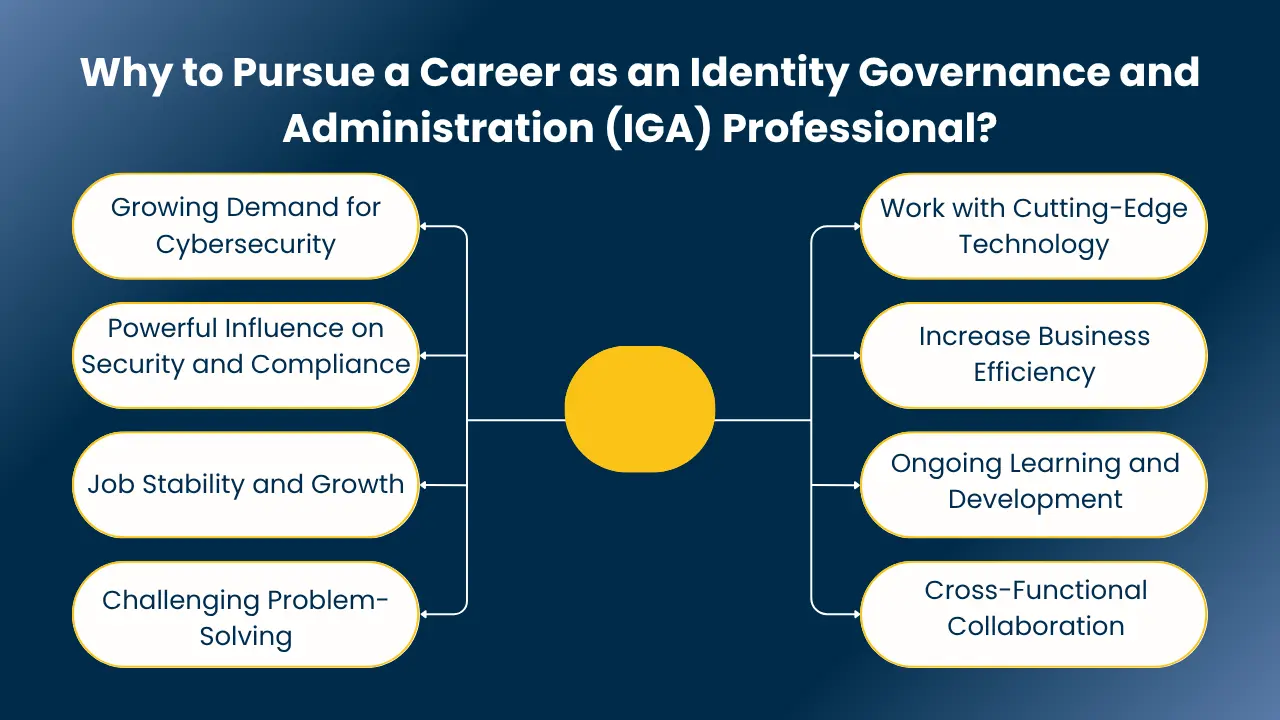
1. Growing Demand for Cybersecurity
With increasing numbers of companies shifting to the cloud and integrating systems, securing sensitive information is essential. IGA professionals play a pivotal role in blocking unauthorized access and cyber attacks.
2. Powerful Influence on Security and Compliance
IGA specialists implement access controls that allow organizations to comply with regulations such as GDPR, HIPAA, and SOX reducing risks by providing users with permissions they need.
3. Job Stability and Growth
The need for IGA experienced professionals is on the rise globally. The career offers secure career stability and well-defined paths for specialization or promotion to leadership roles.
4. Challenging Problem-Solving
You’ll solve complex systems and design smart solutions that address security, usability, and compliance needs. Effective communication enables you to work with both technology teams and business executives effectively.
5. Work with Cutting-Edge Technology
Identity Governance and Administration uses technologies like automation, cloud infrastructure, AI, and machine learning keeping your skills up to date and applicable.
6. Increase Business Efficiency
Through providing effective access control, IGA specialists increase productivity and save costs saving employees’ time without sacrificing security.
7. Ongoing Learning and Development
The career offers plenty of opportunities for developing technical and soft skills, fostering ongoing professional development.
8. Cross-Functional Collaboration
You’ll be working with IT, security, compliance, and business teams, building a strong network and gaining precious acknowledgment across the company.
How Cybersec Trainings Can Help You Build a Successful Career in Identity Governance and Administration?
Start your career in Identity Governance and Administration (IGA) does not just mean theory you need hands-on competence and recognized certifications. That’s where Cybersec Trainings can give you the benefits of identity governance and administration to succeed.
1. Industry-Oriented Curriculum
Our courses cover identity lifecycle and access governance all the way to compliance and technical integration. We refresh the content with the latest tools and trends so you’re ready for today’s challenges.
2. Real-World, Hands-On Training
We don’t just teach concepts you get the opportunity to work alongside real IGA platforms like SailPoint, Saviynt, and Microsoft Entra ID Governance. Simulations and labs let you get comfortable working with real enterprise scenarios.
3. Expert Instruction and Mentorship
Be trained by experienced cybersecurity professionals who provide one-on-one support, allowing you to master tough topics and develop critical problem-solving skills.
4. Certification and Career Readiness
We prepare you for key certifications like CIGE, CIAM, and SC-300 with rigorous training, practice tests, and interview preparation. And help polish your resume for better job prospects.
5. Flexible Learning Options
If you like watching live online classes, self-learning, or weekend batches, we make it easy to balance learning with your busy schedule.
6. Strong Industry Network and Job Support
Our connections to top employers and recruiters give you access. We also offer career guidance and placement assistance to help start or progress in your career.
Conclusion
A career in Identity Governance and Administration offers daunting opportunities to leave a positive impact on organizational compliance and security. As increasing reliance on digital identities intensifies, Identity Governance and Administration professionals are more vital than ever to manage access and mitigate risk. By pursuing technical skills, industry certifications, and experience, you position yourself for lucrative jobs in various industries. Cybersec Trainings provides you with the comprehensive training and hands-on practice needed to excel in the IGA field, resulting in career advancement and safe long-term placement in cybersecurity’s ever-changing landscape.
Understand how Orbus can help your career!
Speak with an Expert Now!
FAQ's
How Long Does It Take to Become a Cybersecurity Engineer?
It typically takes 4 to 6 years to become a cybersecurity engineer. It entails completing a bachelor's degree in a field of study (usually 3-4 years) and then gaining experience and certifications in the field of cybersecurity. Others condense this timeframe via internships, bootcamps, or training programs.
What Degree is Needed to Be a Cybersecurity Engineer
A bachelor's degree in computer science, information technology, cybersecurity, or any other related field is usually necessary to become a cybersecurity engineer. Advanced degrees or professional certifications can further boost career advancement and job opportunities.
What are the 4 Components of IAM?
The four major components of Identity and Access Management (IAM) are:
- Identification – Confirming the identity of a user or system.
- Authentication – Ensuring that the user is, in fact, who they claim to be (e.g., passwords, biometrics).
- Authorization – Permitting or denying access to resources based on policy.
- Accountability – Tracking user activity and access for auditing and compliance.
What is the Difference Between Identity Governance and Administration and IAM?
IAM (Identity and Access Management) covers at large the processes and technologies used to manage digital identities and control access to resources. Identity Governance and Administration (IGA) is a subset of IAM focusing on governance capabilities, including policy enforcement, compliance, risk management, and auditing identity lifecycle and access permissions.
Which Tool is Used for Identity Governance and Administration?
Some of the best Identity Governance and Administration tools are SailPoint IdentityIQ, Saviynt, Oracle Identity Governance, and Microsoft Entra ID Governance. These products help organizations automate identity access management, enforce policies, and maintain compliance.