Cloud security is all about keeping your cloud infrastructure, apps, and data safe. It includes tools and processes that help detect, analyze, and stop threats while keeping everything running smoothly. With so many security tools out there, it can be tricky to figure out which ones you actually need. A good security setup should cover different roles, from threat detection to compliance and access control. In this blog, we’ll break down the top cloud security tools, the best tools for cloud security engineers, and how to choose the right ones for your needs. Let’s dive in!
What Are Cloud Security Tools?
Cloud security tools are software solutions designed to protect your cloud data, applications, and infrastructure. They address security issues like unauthorized access, data privacy, and cloud vulnerabilities. These tools make sure your cloud environment stays safe and complies with industry regulations. They help with tasks like identity management, data encryption, and threat detection, making sure everything is secure.
For cloud security engineers, cloud security monitoring tools are important for keeping everything in check. These tools provide real-time protection, detect vulnerabilities, and help with ongoing monitoring. They work across different cloud setups like IaaS, PaaS, and SaaS, keeping your cloud systems safe and running smoothly.
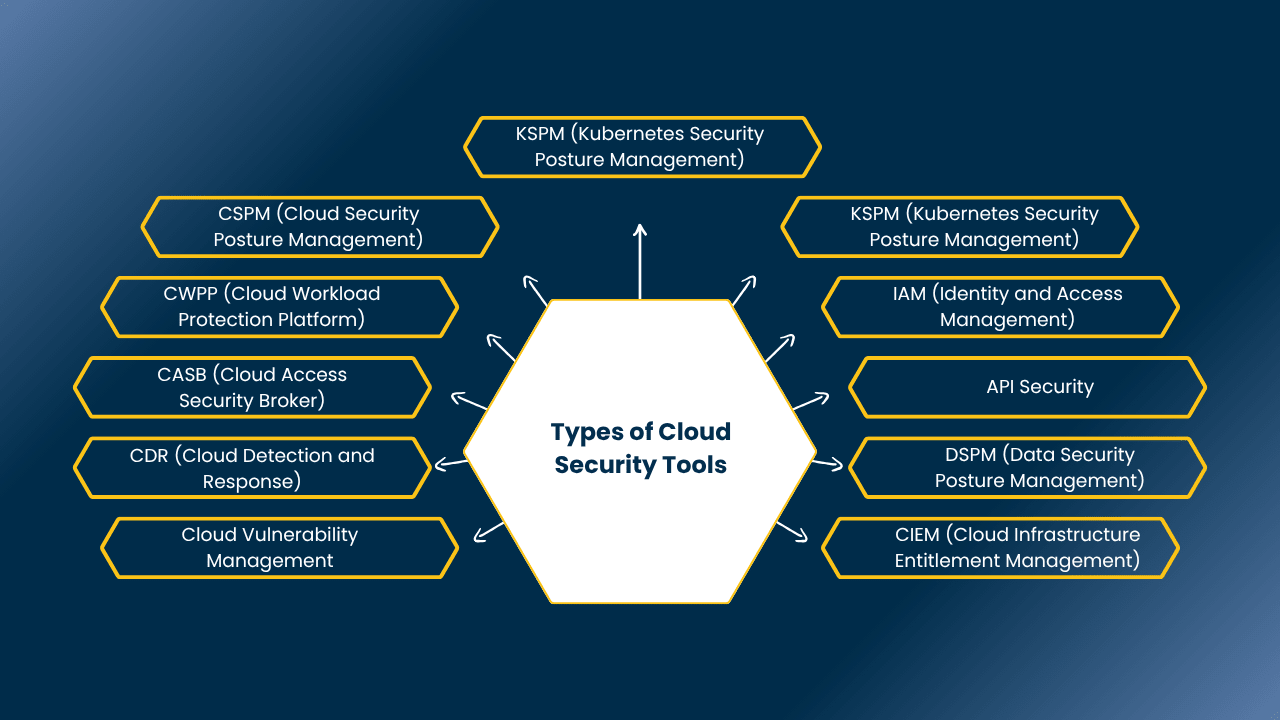
Types of Cloud Security Tools
There are many cloud security tools available, each tackling specific security challenges in cloud environments. Below are some of the main types of cloud security tools to keep your cloud infrastructure secure:
1. CSPM (Cloud Security Posture Management)
CSPM tools automate risk detection and fixing across cloud infrastructures. They offer continuous monitoring and compliance checks, helping your cloud environment stay secure. These tools scan for misconfigurations and compliance issues, providing insights into security weaknesses. With CSPM, you get a centralized view of your cloud security posture and can take proactive steps toward better risk management.
2. CWPP (Cloud Workload Protection Platform)
CWPP tools focus on protecting workloads in cloud environments. They safeguard applications, both hosted and containerized, from various threats. Key features include runtime protection, vulnerability management, and network segmentation. These tools are critical for hybrid and multi-cloud environments, keeping cloud-based applications and services protected from evolving threats.
3. CASB (Cloud Access Security Broker)
Cloud access security broker tools sit between users and cloud service providers. They help enforce security policies, offering visibility into cloud application usage, identifying risks, and managing data access. CASBs are perfect for environments with Bring Your Own Device (BYOD) policies, preventing data breaches and unauthorized access through encryption, access control, and threat prevention.
4. CDR (Cloud Detection and Response)
Cloud Detection and Response tools specialize in identifying and responding to threats in cloud environments. Using advanced analytics and threat intelligence, these tools detect suspicious activities and trigger real-time alerts or automated responses. CDR tools are key for fast threat remediation, minimizing the impact of security breaches.
5. Cloud Vulnerability Management
Cloud vulnerability management tools identify and address security weaknesses in your cloud infrastructure. These tools scan cloud resources for issues like misconfigurations, outdated software, and known vulnerabilities. They prioritize vulnerabilities based on severity, allowing you to tackle the most critical issues first.
6. CIEM (Cloud Infrastructure Entitlement Management)
CIEM tools manage user access entitlements and permissions in cloud environments, preventing excessive privileges. These tools help control access to sensitive resources, reducing the risk of unauthorized access and data breaches. CIEM tools follow the principle of least privilege, making your cloud environment more secure.
7. DSPM (Data Security Posture Management)
DSPM tools focus on securing and monitoring data in cloud environments. These tools help identify risks related to data storage, access, and transfer, while also making sure compliance with data governance standards is maintained. DSPM tools provide real-time insights into data security, helping detect misconfigurations and enforce data protection policies. They can also automatically fix vulnerabilities to lower the risk of data exposure.
8. API Security
API security tools protect APIs from exploitation by malicious actors. APIs are crucial for communication between applications and services, so securing them is important to prevent data breaches. These tools offer features like authentication, traffic management, and threat detection, making sure that APIs remain secure and comply with organizational security policies.
9. IAM (Identity and Access Management)
IAM tools manage user identities and control access to cloud resources. These tools enforce secure login practices, such as Single Sign-On (SSO) and Multi-Factor Authentication (MFA), preventing unauthorized access. IAM tools also track user activities, making it easier to monitor compliance and maintain secure cloud environments.
10. KSPM (Kubernetes Security Posture Management)
KSPM tools are designed specifically to secure Kubernetes clusters. They analyze security risks within Kubernetes environments, helping protect cluster control planes and worker nodes. KSPM works alongside broader CSPM solutions, offering additional protection in large-scale, distributed cloud environments.
11. RBAC (Role-Based Access Control)
RBAC tools manage access to cloud resources by assigning specific permissions to different roles within your organization. These tools help prevent over-privileged access, reducing the risk of unauthorized changes or data leaks. Only authorized users can perform sensitive actions like creating or deleting users.
Also Read: Penetration Testing Course and Training in Mumbai
Open Source Cloud Computing Security Tools
Here are some great open-source cloud security tools that help protect your cloud infrastructure from security vulnerabilities and misconfigurations.
1. OpenVAS
OpenVAS, maintained by Greenbone, is a powerful vulnerability scanner that supports both unauthenticated and authenticated security testing. It’s perfect for scanning large networks and various protocols, and its customizability makes it one of the best cloud security tools for comprehensive vulnerability assessments.
Key Features of OpenVAS:
- Supports both unauthenticated and authenticated tests, covering a wide range of security needs.
- Works across different network environments, supporting various internet and industrial protocols.
- Provides performance tuning for large-scale scans, ideal for extensive networks.
- Allows users to create custom vulnerability tests with an internal programming language.
- Regular updates to its vulnerability test feeds make sure the scanner stays current with the latest security threats.
2. Trivy
Trivy, developed by Aqua, is a versatile security scanner that identifies vulnerabilities in various cloud environments. It scans container images, file systems, remote Git repositories, virtual machine images, Kubernetes configurations, and AWS environments, making it an all-in-one tool for cloud security monitoring tools.
Key Features of Trivy:
- Scans container images, file systems, Git repositories, virtual machine images, Kubernetes, and AWS environments.
- Identifies known vulnerabilities, misconfigurations, sensitive data, and software dependencies.
- Supports various programming languages and platforms, ensuring extensive coverage.
- Easy installation via Docker, Homebrew, or GitHub.
- Integrates with GitHub Actions, Kubernetes operators, and Visual Studio Code plugins.
- Offers early access to features with canary builds, although these may contain bugs.
3. CloudMapper
CloudMapper is tailored for Amazon Web Services (AWS) environments. Initially a network visualization tool, it now includes auditing features to help detect security issues in AWS accounts. This is a must-have tool for auditing and fixing AWS security misconfigurations.
Key Features of CloudMapper:
- Focuses on AWS environments, providing network configuration insights and security vulnerability analysis.
- Detects unused resources, public hosts, and port ranges, among other misconfigurations.
- Includes commands like audit, collect, find_admins, and report for generating security reports.
- Works on both macOS and Linux, with easy setup using Python and other dependencies.
- Customizable with the ability to create private commands tailored to specific security needs.
4. CloudSploit
CloudSploit, also developed by Aqua, is an open-source tool that identifies security risks and vulnerabilities in cloud infrastructure accounts. It supports major cloud platforms like AWS, Azure, GCP, OCI, and GitHub, making it one of the top cloud security tools for cloud infrastructure management.
Key Features of CloudSploit:
- Works with major cloud platforms like AWS, Azure, GCP, OCI, and GitHub.
- Provides self-hosted and Aqua Wave hosted deployment options.
- Only requires read-only access to cloud accounts for vulnerability detection.
- Offers flexible configuration through config files, credential files, or environment variables.
- Includes compliance scans for HIPAA, PCI, and CIS Benchmarks.
- Generates reports in various formats, including CSV, JSON, and XML, making integration with other tools easy.
5. OSSEC
OSSEC is an open-source security platform that integrates host-based intrusion detection (HIDS), log monitoring, and SIM/SIEM features. It provides a broad approach to cloud security tools, focusing on monitoring, detecting, and responding to various system security threats.
Key Features of OSSEC:
- Combines HIDS, log monitoring, and SIM/SIEM capabilities, covering a wide range of security aspects.
- Offers File Integrity Monitoring (FIM) and attack detection, including threats like SSH brute force attacks.
- Supports an active community via platforms like Slack and Discord, offering continuous updates and support.
- Regular updates to the platform via GitHub make sure ongoing improvements and enhancements.
Read More: SailPoint IdentityIQ Jobs: Career Opportunities and Growth
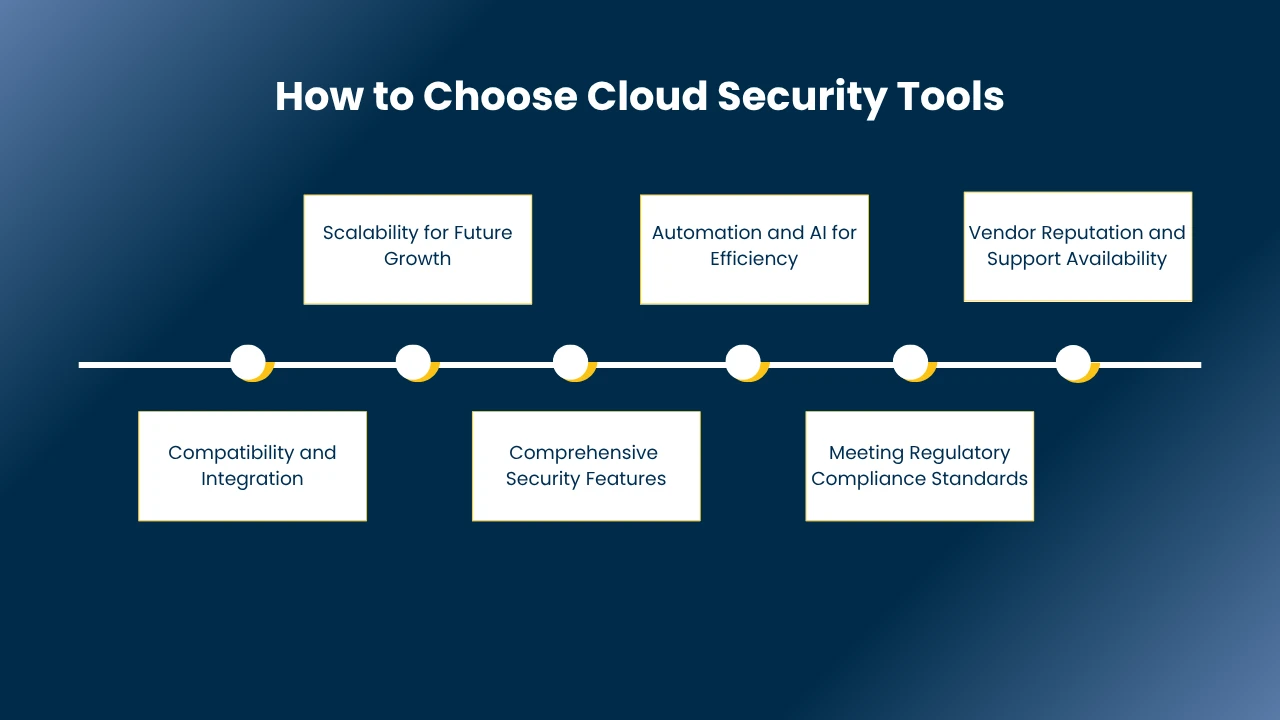
How to Choose Cloud Security Tools
When choosing cloud security tools, here are some key factors to keep in mind to make sure you pick the right solution for your needs:
1. Compatibility and Integration
Make sure the tools you choose work well with your existing cloud infrastructure and security systems. This ensures everything integrates smoothly, minimizes disruptions, and allows you to leverage your current investments. It’s important that the tool fits well with your cloud service providers and is compatible with other security solutions like cloud access security broker tools or vulnerability management systems.
2. Scalability for Future Growth
Select tools that can scale with your cloud environment. As your cloud resources grow or shrink, the security tools must adapt to the changes without affecting performance or security. This makes sure that your protection remains strong, no matter how your cloud usage evolves.
3. Comprehensive Security Features
Look for cloud security tools that offer broad protection across all areas of your cloud environment. Tools like cloud security monitoring tools or cloud data security tools should cover workload protection, data security, threat detection, compliance, and network security. Tools with a wide range of security functions help reduce complexity and speed up incident response times.
4. Automation and AI for Efficiency
Consider tools that feature automation and artificial intelligence. These capabilities help quickly detect and respond to threats, which reduces the burden on your security teams and minimizes human error. Automation can also speed up response times and improve overall security management.
5. Meeting Regulatory Compliance Standards
Make sure that the tools you select meet the regulatory requirements for your industry. Compliance with data protection standards, privacy laws, and specific regulations is important. Choosing tools that support compliance helps protect your organization from potential fines and legal challenges.
6. Vendor Reputation and Support Availability
Assess the reputation of the vendor and the quality of support they provide. Reliable vendor support is crucial for troubleshooting, updates, and best practice guidance. Additionally, check out the community and resources around the tool for extra help and integration opportunities.
When looking for top cloud security tools or even cloud security tools free, these factors will guide you toward the best cloud security tools for your needs. Use a cloud security tools list to compare options and find the perfect fit for your cloud security strategy.
Conclusion
Selecting the right cloud security tools is crucial for protecting your cloud infrastructure, applications, and data. Tools such as cloud access security broker tools provide enhanced security measures for access control and threat detection. It’s important to choose tools that are compatible with your existing cloud environment, can scale with growth, and offer automated protection. Investing in the right cloud security tools helps safeguard your assets, maintain compliance, and mitigate potential security risks effectively.