How to Become Ethical Hacker after Doing cPent Certification in 2025

In the modern age of cyberspace, where threats to the digital space are evolving in complexity every day, ethical hackers are the frontline security against dangerous attacks on critical systems and data. These are the security warriors who guard an organization’s digital presence from being attacked, finding out the vulnerabilities first so that they cannot be exploited. If you’ve already obtained your CPENT (Certified Penetration Testing Professional) certification, you’re halfway to becoming a cybersecurity asset to be reckoned with.
But what’s next? Making a career switch to ethical hacking may be the best decision you ever make. By pairing technical competence with top-notch certifications and experienced mentorship, you can establish a fulfilling and future-proof penetration testing cyber security career. Here, we’ll take you through the process of how to be an effective ethical hacker once you have passed the CPENT certification and demonstrate to you how Orbus can guide and speed you in becoming an in-demand cybersecurity professional.
What is Ethical Hacking?
Ethical hacking involves legally invading computer systems, networks, or software to locate and fix security vulnerabilities. Ethical hackers are otherwise known as white-hat hackers. They use the same methods and tools as criminal hackers. But they do so with proper authorization. Their aim is to help organizations protect their defenses, prevent cyberattacks, and protect sensitive data. Ethical hacking is an essential part of cybersecurity in today’s world. Especially as threats become more sophisticated and more common.
What Do Ethical Hackers Do?
Ethical hackers are security professionals. They duplicate cyberattacks to find vulnerabilities in systems, networks, or applications. They are not the same as malicious hackers. They work with full authorization and legal boundaries. Their job is to pretend to be an attacker with the same tools and techniques. But with the objective of strengthening security. Further, they provide comprehensive reports, recommend patches, and work with security teams. Further, they secure systems from real threats.
What are the Key Skills Required for Ethical Hackers?
To thrive as an ethical hacker, it’s not just about curiosity or knowing a few tools it’s about combining technical expertise with real-world problem-solving. Ethical hackers need to think like attackers, but act with integrity and precision. Here are some of the most essential skills you’ll need to master:
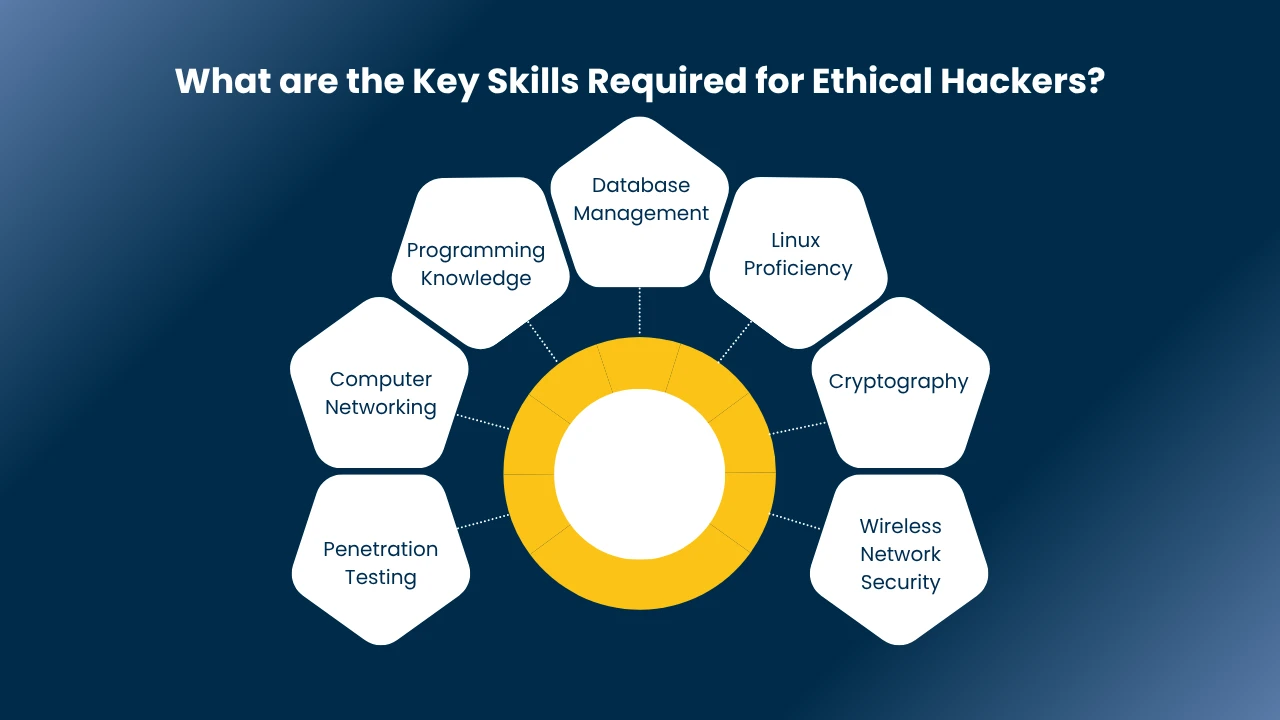
1. Penetration Testing
Penetration testing is the core of ethical hacking the process of simulating cyberattacks to expose weaknesses before malicious hackers do. This involves steps like reconnaissance (gathering information), scanning, exploiting weaknesses, and finally reporting results in a structured format. Ethical hackers employ tools like Metasploit, Nmap, Wireshark, and Hashcat to perform these tests efficiently and ethically.
2. Computer Networking
A strong understanding of how computer networks and systems communicate is vital. Ethical hackers must grasp concepts like IP addressing, routing, switching, subnetting, and supernetting. How data travels across networks enables identification of potential entry points and vulnerabilities in infrastructure, especially in enterprise systems that are larger in size.
3. Programming Knowledge
While you don’t have to be an extreme developer, knowing programming languages gives you a definite edge. Python, C, JavaScript, and PHP are especially valuable to know for scripting, building exploits, or automation. It’s also handy while analyzing malware or learning how a code weakness can be exploited.
4. Database Management
Data is the most valuable asset of the majority of organizations, and hackers target poorly secured databases. Ethical hackers must be able to analyze the security of databases like MySQL, SQL Server, or Oracle. Knowing how to write and read CRUD operations (Create, Read, Update, Delete) and SQL queries is essential for finding injection vulnerabilities or misconfigurations.
5. Linux Proficiency
A majority of ethical hacking tools are constructed to operate in Linux. It is the ideal OS for those who work in cybersecurity due to its flexibility and open-source programming. Command line skills, working with files, permission setting, and Bash or Python scripting are highly desirable skills.
6. Cryptography
Cryptography is a very important aspect in securing sensitive data. Ethical hackers need to understand encryption techniques, digital certificates, hashing algorithms, and secure communication protocols to gauge the robustness of data security and determine vulnerabilities in encryption usage.
7. Wireless Network Security:
With the proliferation of mobile and wireless technologies, wireless network security has become crucial. Ethical hackers should be competent in examining Wi-Fi security protocols (such as WPA2, WPA3), recognizing rogue access points, and discovering weak encryption or default settings that can be exploited by attackers.
How Do You Become an Ethical Hacker After CPENT Certification?
CPENT certification provides a solid foundation, but becoming a successful ethical hacker takes more than just passing the exam. You will need to practice by hand, pick the right area of focus, and continue to hone your skills. This is a step-by-step process to move from CPENT certification to achieving a successful career as an ethical hacker:

1. Set Real-World Experience
After you have obtained your CPENT certification, it’s now time to put your skills to work. Get internships, freelance, or lab environments where you can apply penetration tests and security audits.
2. Participate in Bug Bounty & CTF Challenges
Bug bounty platforms and Capture the Flag (CTF) challenges are ideal for hands-on practice. They develop your skills, as well as make you noticed in the field of cybersecurity.
3. Choose a Specialization
Ethical hacking is a wide area web apps, networks, wireless, social engineering, etc. Choose a niche that you are interested in and specialize more to stand out in that niche.
4. Stay Current with Industry Trends
Cybersecurity evolves rapidly. Stay current with blogs, news websites, and forums of well-known sources to learn about new vulnerabilities, tools, and techniques used by attackers and defenders.
5. Build a Strong Portfolio
Showcase your work through write-ups, GitHub projects, or a personal blog. Document the tools you’ve used, challenges you’ve solved, and what you’ve learned this helps recruiters see your potential.
What are the Certifications for Ethical Hacker?
To establish a career in ethical hacking, certifications are necessary. They authenticate your skills, enhance your credibility, and provide access to job opportunities with leading penetration testing companies in India. Although CPENT (Certified Penetration Testing Professional) is a well-respected advanced-level certification, it’s just one step in your cybersecurity path. Most ethical hackers in India opt to obtain several certifications to specialize in penetration testing, network defense, cyber forensics, or security management.
These certifications also reflect your commitment to remaining up-to-date in the constantly evolving landscape of cybersecurity. Whether you are just starting out or looking to advance to a senior position, obtaining the proper certifications can significantly boost your career. Some of the best certifications in ethical hacking and cybersecurity are listed below:
Core Ethical Hacking Certifications
Certified Ethical Hacker (CEH): An introductory penetration testing certification that familiarizes you with the attacker’s mindset, tools, and techniques both applied by malicious attackers and ethical hackers. It is an in-depth study of system hacking, footprinting, threats from malware, and social engineering.
- Offensive Security Certified Professional (OSCP): A practical, performance-oriented certification that requires you to implement real-world penetration testing under the pressure of a time limit. Well known across the industry for its strict examination format.
- CompTIA PenTest+: A hands-on certification that is suitable for intermediate-level IT professionals. It deals with detection, exploitation, reporting, and vulnerability management within a network system.
- Certified Penetration Testing Engineer (CPTE): This certification gives an end-to-end knowledge of penetration testing techniques, from reconnaissance to post-exploitation methods.
- GIAC Penetration Tester (GPEN): Concerned with testing target networks and identifying weaknesses using a structured method. GPEN is an excellent option for IT professionals looking to prove extensive knowledge of pen testing processes.
Advanced Security & Specialization Certifications
- CISSP (Certified Information Systems Security Professional): Designed for seasoned security professionals, CISSP is best suited for positions that entail designing and directing an organization’s overall security stance.
- CISA (Certified Information Systems Auditor): Is geared towards auditing, control, and assurance, making it worth it for those working in IT compliance and governance.
- CISM (Certified Information Security Manager): Is best suited for those who are managing and directing information security programs. It combines technical understanding with strategic planning.
- CHFI (Computer Hacking Forensic Investigator): For experts in identifying hacking attacks, extracting evidence in a legitimate manner, and reporting cybercrime.
- CREST Registered Penetration Tester: Internationally recognized, particularly in the UK and Europe. It is focused on professional practice and effective penetration testing expertise.
Niche & Supporting Skills Certifications
- Reverse Engineering: Crucial to the analysis of malware, how malicious code works, and building effective countermeasures.
- Cryptography Certifications: These include the basics of hacking and penetration testing, and secure communications, encryption methods, key management, and data protection methodologies.
- Social Engineering Courses: Learn the human aspect of cybersecurity how criminals trick people into sharing secrets, and how to protect against it.
- Network Security & Real-World Hacking Courses: These provide hands-on training labs to mimic real-world cyber-attacks and countermeasures, allowing the learning of practical uses.
What is the Ethical Hacker Salary Data?
In India, the salary of an ethical hacker depends on experience, skill set, and certifications. Beginners can expect a decent starting package, and over time, knowledge, and credentials such as CPENT, salaries increase substantially.
Here’s a close analysis of average ethical hacker salary in india ranges based on experience:
| Experience Level | Average Salary |
|---|---|
| Entry-Level (Less than 1 year) | ₹4,50,000 – ₹5,50,000 |
| Mid-Level (1–4 years) | ₹6,00,000 – ₹8,00,000 |
| Senior Level (5–9 years) | ₹8,00,000 – ₹12,00,000 |
| Lead/Expert Level (10+ years) | ₹14,00,000+ |
These numbers may vary based on location, company size, and certifications. Ethical hackers with global credentials and hands-on expertise in areas like cloud security, forensics, and advanced penetration testing are in particularly high demand.
How Orbus Can Help in Becoming Ethical Hacker?
If you’re aiming to become a skilled ethical hacker, Orbus International offers the perfect launchpad. Our CEH program combines expert-led training, hands-on labs, and industry-recognized certification to help you stand out in the cybersecurity field.
| Features | Details |
|---|---|
| Course Name | Certified Ethical Hacker (CEH) EC-Council Accredited |
| Course Duration | 40 hours (Weekday & Weekend batches available) |
| Mode of Delivery | Online Instructor-Led / Classroom Training |
| Course Fees | Starting from ₹35,000 |
| Eligibility | Basic networking knowledge preferred (beginners welcome) |
| What You will Learn | Footprinting, scanning, system hacking, web & wireless security, cryptography, cloud security |
| USPs of Orbus |
|
Conclusion
To become an ethical hacker once you have earned your CPENT certification is a wise career decision as well as a logical step in the field of cybersecurity. With the increased need for expert professionals, this is the ideal time to become specialized. By honing your technical expertise, getting hands-on practice, and selecting the ideal training partner such as Orbus, you can walk into this high-demanding position with confidence. Let your CPENT roots give you the strength to succeed in the world of ethical hacking.
Understand how Orbus can help your career!
Speak with an Expert Now!
FAQ's
What is the Cpent certified person's salary?
C|PENT-certified individuals are some of the highest-paid professionals in the cybersecurity industry, with a variety of exciting job opportunities to choose from. Freshers can expect salaries starting from ₹4.5 LPA, while senior-level professionals can earn up to ₹29.2 LPA.
What is the difference between Cpent and CEH?
Although both CEH (Certified Ethical Hacker) and CPENT (Certified Penetration Testing Professional) are cybersecurity oriented, CEH deals with the core concepts of ethical hacking, providing a wide overview. Compared to CPENT, it goes a step ahead by focusing on penetration testing skills and experience with hands-on practice using real-world attack cases.
Does CPent expire?
The EC-Council's CPENT (Certified Penetration Testing Professional) certification is for a three-year period from the certification date.
Difference between penetration tester and ethical hacker?
- Although often used interchangeably, "ethical hacker" is a broader term that covers a range of cybersecurity practices.
- Penetration testing, on the other hand, is a specialized area within ethical hacking that involves simulating real-world attacks to uncover vulnerabilities in a targeted system or network.




