In the fast-changing digital era of today. We all are aware that threats through cyberspace are getting more advanced and so will our denseness. Thus, tools of ethical hacking have an important role to play in mapping system vulnerabilities before anyone else can do so. Thus, in this blog, we shall discuss the top 100 ethical hacking tools in 2025. They are categorized for easy understanding and use.
In addition, whether you are conducting network scans, mimicking actual-world attacks, or using AI for discovering sophisticated threats. These tools make ethical hackers more capable. Also, be it beginners or advanced professionals, this guide is your go-to toolbox for ethical cyber security activities.
What are Hacking Tools and Software?
Ethical hacking tools are specialized software used by cybersecurity professionals to test, analyze, and strengthen digital systems. These tools simulate cyberattacks, detect vulnerabilities, and help secure networks and applications. From enumeration tools in ethical hacking to footprinting tools in ethical hacking, each serves a unique role in assessing risk. While some hacking tools can be misused, ethical hackers use them legally to protect data and infrastructure. Whether it’s Linux ethical hacking tools tools for Android, or Metasploit, these solutions are essential for modern cyber defense.
What is the Importance of Hacking Software?
Ethical hacking tools play a critical role in modern cybersecurity by proactively identifying and resolving vulnerabilities before they can be exploited. These tools allow organizations to evaluate their defenses from a hacker’s perspective, strengthening their overall security posture. By using tools required for ethical hacking, businesses can protect sensitive data, reduce the risk of breaches, and ensure compliance with regulations like GDPR and HIPAA.
Regular assessments with ethical hacking tools and techniques also help organizations understand attack vectors, mitigate threats efficiently, and avoid costly incidents. Whether deploying ethical hacking tools for Windows or Linux ethical hacking tools, the goal is to detect flaws early, reduce potential financial and reputational damage, and boost stakeholder trust. Additionally, these tools contribute to employee awareness and cybersecurity training by exposing real-world vulnerabilities and risks.
Top 100 Ethical Hacking Tools to Watch Out For in 2025
In the ever-evolving cybersecurity landscape, ethical hackers and penetration testers rely on powerful tools to detect vulnerabilities, strengthen defenses, and simulate attacks. These tools span various categories such as reconnaissance, web application testing, password cracking, wireless network assessment, exploitation, and more. Below is a categorized, concise guide to the top 100 ethical hacking tools in 2025.
1. Reconnaissance & OSINT Tools
These tools gather publicly available information (emails, domains, social profiles, etc.) to identify potential vulnerabilities before launching an attack.
| S.No | Tool | Description | Key Features |
|---|---|---|---|
| 1. | Maltego | Graph-based link analysis tool for OSINT investigations | Visual relationship mapping, 100+ transforms, API integrations |
| 2. | theHarvester | Email, subdomain, and hostname collector | Multi-source data gathering, stealth reconnaissance, HTML reports |
| 3. | Recon-ng | Recon framework with modular architecture | API key management, data export, CLI interface |
| 4. | SpiderFoot | Automated OSINT and threat intel scanner | 150+ sources, custom scans, web interface |
| 5. | FOCA | Metadata and information extractor | PDF/DOC scraping, server fingerprinting |
| 6. | Shodan | Search engine for Internet-connected devices | Filtered searches, vulnerability exposure, live host detection |
| 7. | Amass | DNS enumeration and asset discovery | Subdomain enumeration, graphing, passive + active modes |
| 8. | Censys | Hosts and certificate discovery engine | Advanced filtering, search by protocol or certificate |
| 9. | DNSdumpster | Online domain research tool | DNS mapping, IP resolution, email tracking |
| 10. | Google Dorking | Manual search engine-based OSINT | Advanced query building, real-time footprinting |
2. Web Application Security Testing Tools
These tools are essential for testing web apps for vulnerabilities like XSS, SQLi, CSRF, and authentication flaws.
| S.No | Tool | Description | Key Features |
|---|---|---|---|
| 1. | Burp Suite | Integrated platform for web app testing | Intercept proxy, scanner (Pro), extensible plugins |
| 2. | OWASP ZAP | Open-source web application security scanner | Passive + active scanning, spidering, GUI-based |
| 3. | SQLMap | Automates detection/exploitation of SQLi | DB fingerprinting, data exfiltration, OS command execution |
| 4. | Nikto | Web server vulnerability scanner | Checks 6000+ issues, outdated software detection |
| 5. | Vega | GUI-based web vulnerability scanner | XSS + SQLi detection, proxy scanner, custom scripting |
| 6. | Wapiti | Black-box web app scanner | Session handling, report export, crawl+attack separation |
| 7. | Arachni | Modular and high-performance scanner | JavaScript crawling, plugin support, login sequence testing |
| 8. | WebScarab | OWASP proxy tool for manual testing | HTTP/HTTPS manipulation, session analysis |
| 9. | Skipfish | Recon tool for high-speed web vulnerability scanning | Sitemap generation, code injection detection |
| 10. | IronWASP | Extensible platform for testing web apps | Plugin support, scanner + manual tools |
Also Read: Top 10 Ethical Hacking Course in Delhi: Duration & Certification
3. Wireless Hacking Tools
Used to assess the security of Wi-Fi networks, detect rogue access points, and capture handshakes.
| S.No | Tool | Description | Key Features |
|---|---|---|---|
| 1. | Aircrack-ng | Suite for WEP/WPA cracking | Packet sniffing, deauth attacks, GPU acceleration |
| 2. | Kismet | Wireless detector/sniffer/IDS | Hidden SSID detection, multi-device support |
| 3. | Reaver | WPS PIN brute-force attack tool | WPA/WPA2 key recovery, pause/resume, logging |
| 4. | Wifite2 | Automates Wi-Fi attacks | Auto-targeting, handshake capture, Reaver integration |
| 5. | Fern WiFi Cracker | GUI tool for wireless auditing | WPA/WEP cracking, network discovery, session hijacking |
| 6. | CoWPAtty | Brute-force WPA2 cracker | PMK analysis, dictionary attacks |
| 7. | Bully | C-based WPS brute-forcer | Optimized performance, crash resistance |
| 8. | InSSIDer | Wi-Fi network scanner | Channel overlap detection, signal analysis |
| 9. | Wifiphisher | Rogue AP phishing toolkit | Credential capture, man-in-the-middle attacks |
| 10. | Airgeddon | Wireless pentesting multi-tool | Evil twin attacks, DoS, deauth management |
4. Password Cracking Tools
These are the best ethical hacking tools to help test password strength via brute force, dictionary attacks, rainbow tables, or hash cracking.
| S.No | Tool | Description | Key Features |
|---|---|---|---|
| 1. | John the Ripper | Fast password cracker | Multi-platform, rule-based, hash auto-detect |
| 2. | Hashcat | GPU-accelerated hash cracker | 300+ algorithms, session management, distributed cracking |
| 3. | Hydra | Parallelized login cracker | 50+ protocols, brute-force + dictionary, CLI-based |
| 4. | Medusa | Fast, scalable login brute-forcer | Multi-threaded, module-based, user-pair support |
| 5. | Cain and Abel | Windows-only password recovery tool | Sniffing, brute-force, cryptanalysis |
| 6. | RainbowCrack | Uses rainbow tables to crack hashes | GPU acceleration, hash lookup speed |
| 7. | L0phtCrack | Password auditing and recovery tool | Brute force + dictionary + hybrid attacks |
| 8. | CrackStation | Online hash cracking using wordlists | Supports MD5/SHA1, educational tool |
| 9. | OphCrack | Windows password cracker via rainbow tables | Live CD support, no installation needed |
| 10. | THC Hydra | Variant of Hydra for network protocols | SSH/HTTP/FTP support, flexible scripting |
Also Read: Top 10 Ethical Hacking Course in Ahmedabad: Duration & Certification
5. Exploitation & Payload Generation Tools
These tools generate payloads or exploit known vulnerabilities in systems, apps, and networks.
| S.No | Tool | Description | Key Features |
|---|---|---|---|
| 1. | Metasploit | Ethical hacking with metasploit the penetration testing tool is popular framework for developing exploits | Module-based, payload creation, database integration |
| 2. | BeEF | Exploits web browser vulnerabilities | Hooking browser sessions, pivoting attacks |
| 3. | Social-Engineer Toolkit | Framework for social engineering attacks | Phishing, credential harvesting, cloning sites |
| 4. | Empire | Post-exploitation C2 framework | Fileless agents, PowerShell + Python, lateral movement |
| 5. | Mimikatz | Credential extraction tool for Windows | Dumping hashes, pass-the-hash, Kerberos ticket theft |
| 6. | Veil Framework | Payload generator that evades antivirus | Obfuscation, AV evasion, Metasploit integration |
| 7. | XploitGPT | AI-assisted exploit generation tool | Reverse shell creation, obfuscation breakdown |
| 8. | AutoSploit | Links Shodan with Metasploit for automation | Target auto-selection, payload deployment |
| 9. | Armitage | GUI front-end for Metasploit | Team collaboration, exploit suggestions |
| 10. | PowerSploit | PowerShell-based post-exploitation scripts | Code execution, privilege escalation, info gathering |
6. AI-Powered Hacking Tools
These tools use machine learning or generative AI to accelerate reconnaissance, code review, malware detection, and response automation.
| S.No | Tool | Description | Key Features |
|---|---|---|---|
| 1. | ReconAI | AI + OSINT concept for automated recon | GPT + SpiderFoot/Maltego, pattern recognition, no fixed UI |
| 2. | HackerAI | AI-based code vulnerability analyzer | Unsafe input detection, static review, logic flaw hunting |
| 3. | Microsoft Security Copilot | Microsoft’s AI assistant for security | Alert summarization, threat detection, automated response |
| 4. | Cortex XDR | ML-powered XDR by Palo Alto Networks | Behavioral analytics, credential abuse tracking |
| 5. | AI-Hunter | AI-based threat detection inside networks | Beaconing/lateral movement tracking, live traffic analysis |
| 6. | ThreatGPT | GPT-powered red teaming tool | MITRE mapping, APT simulation, tailored attack path generation |
| 7. | BloodHound + AI | AD attack path mapping + AI insights | Graph AI analytics, privilege escalation path prediction |
| 8. | Elastic Security + ML | ELK-based anomaly detection engine | ML for brute force, data exfiltration, custom rules |
| 9. | AutoSploit (AI ver.) | AI-enhanced Shodan-Metasploit integration | Target prioritization, smart payload deployment |
| 10. | XGPT Code Auditor | GPT tool for auditing suspicious scripts | Decoding, code explanation, exploit detection |
Also Read: Ethical Hacking Course in Gurgaon: Learn the Skills You Need in 2025
7. Network Scanning & Mapping Tools
Crucial for discovering active hosts, ports, services, and network topology.
| S.No | Tool | Description | Key Features |
|---|---|---|---|
| 1. | Nmap | Industry-standard network mapper | Port scanning, OS detection, scripting engine |
| 2. | Zenmap | GUI for Nmap | Visual scan results, beginner-friendly |
| 3. | Angry IP Scanner | Lightweight IP and port scanner | Fast scanning, export to CSV/HTML/XML |
| 4. | Advanced IP Scanner | IP scanner for Windows | Remote shutdown, MAC address detection |
| 5. | Fping | Fast ICMP ping sweeper | Bulk host pinging, latency tracking |
| 6. | SuperScan | Multi-function port scanner | Host discovery, banner grabbing |
| 7. | Unicornscan | High-performance asynchronous scanner | TCP/UDP scanning, large network handling |
| 8. | Netcat | Versatile network tool | Port scanner, file transfer, remote shell |
| 9. | NetScanTools | Network diagnostics toolkit | DNS lookup, ping, traceroute, WHOIS |
| 10. | Nessus | Enterprise-grade vulnerability scanner | Patch management, plugin updates, risk scoring |
8. Forensics & Analysis Tools
Used to investigate breaches, recover data, and analyze system artifacts.
| S.No | Tool | Description | Key Features |
|---|---|---|---|
| 1. | Autopsy | Open-source digital forensics platform | Timeline analysis, file carving, keyword search |
| 2. | EnCase | Enterprise forensics software | Memory forensics, mobile + endpoint support |
| 3. | FTK | Forensic imaging & investigation tool | Email parsing, registry analysis, file decryption |
| 4. | SIFT Workstation | DFIR toolkit built on Ubuntu | Volatility, Plaso, Sleuth Kit, comprehensive scripts |
| 5. | X-Ways Forensics | Lightweight forensic suite | Low resource usage, portable, advanced hex viewer |
| 6. | Helix3 Pro | Incident response live CD | Memory imaging, disk cloning, registry analysis |
| 7. | Foremost | Command-line file recovery tool | File carving from images, simple configuration |
| 8. | Scalpel | Successor to Foremost with enhancements | Faster carving, custom config for file headers/footers |
| 9. | The Sleuth Kit | Open-source forensic investigation libs | Timeline, file system analysis, disk image exploration |
| 10. | CAINE | Linux distro for digital forensics | GUI-based tools, volatile data collection, live USB boot |
Also Read: Certification with a Top Ethical Hacking Course in Bihar – 2025
9. Social Engineering & Phishing Tools
Used to simulate or perform real-world attacks on human vulnerabilities.
| S.No | Tool | Description | Key Features |
|---|---|---|---|
| 1. | King Phisher | Phishing simulation tool | Credential harvesting, email templates, campaign stats |
| 2. | GoPhish | Lightweight phishing framework | Custom landing pages, tracking, user management |
| 3. | Evilginx | MITM phishing tool with 2FA bypass | Session hijacking, SSL certificate spoofing |
| 4. | Wifiphisher | Rogue AP + phishing combo | Login portal cloning, malware injection |
| 5. | Ghost Phisher | Wireless phishing toolkit | AP emulation, web spoofing, credential logging |
| 6. | Credential Harvester | Part of SET toolkit | Website cloning, credential capture |
| 7. | Maltego (OSINT use) | Link analysis tool | Person/company footprinting, data fusion |
| 8. | ReelPhish | Automated 2FA phishing attack tool | Real-time proxying, supports multiple login pages |
| 9. | SET Toolkit | Social engineering attack framework | SMS/email spoofing, Java payloads, website cloning |
| 10. | HiddenEye | Automated phishing tool | Instagram/Google page clones, real-time login capture |
10. Miscellaneous Tools
These tools serve various purposes including SSL inspection, credential extraction, debugging, and endpoint monitoring that don’t strictly fall into other categories.
| S.No | Tool | Description | Key Features |
|---|---|---|---|
| 1. | OpenSSL | Toolkit for SSL/TLS cryptographic functions | Certificate creation, data encryption, secure communication |
| 2. | Pcredz | Credential extractor from packet captures | Supports HTTP, FTP, POP3, IMAP, SMTP, Telnet, logs all credentials |
| 3. | Mimikatz | Credential dumping tool for Windows | Password hash dumping, pass-the-hash, Kerberos ticket manipulation |
| 4. | Sysinternals Suite | Windows debugging and system analysis suite | 80+ tools for diagnostics, file monitoring, memory inspection |
| 5. | GPG | Encryption tool for secure communication | Email encryption, file signing, key pair generation |
| 6. | Rubeus | Kerberos abuse tool | Ticket harvesting, Golden/Silver Ticket attacks |
| 7. | SMBMap | SMB enumeration and share auditing | Credential validation, share permission auditing |
| 8. | Responder | LLMNR/NBT-NS/MDNS poisoner | Credential theft via spoofed responses, rogue authentication |
| 9. | CrackMapExec | Post-exploitation tool for Active Directory | Lateral movement, command execution, credential spraying |
| 10. | PsExec | Remote execution tool by Sysinternals | Run processes on remote systems without manual login |
Also Read: 50 Ethical Hacking Interview Questions and Answers You Must Know
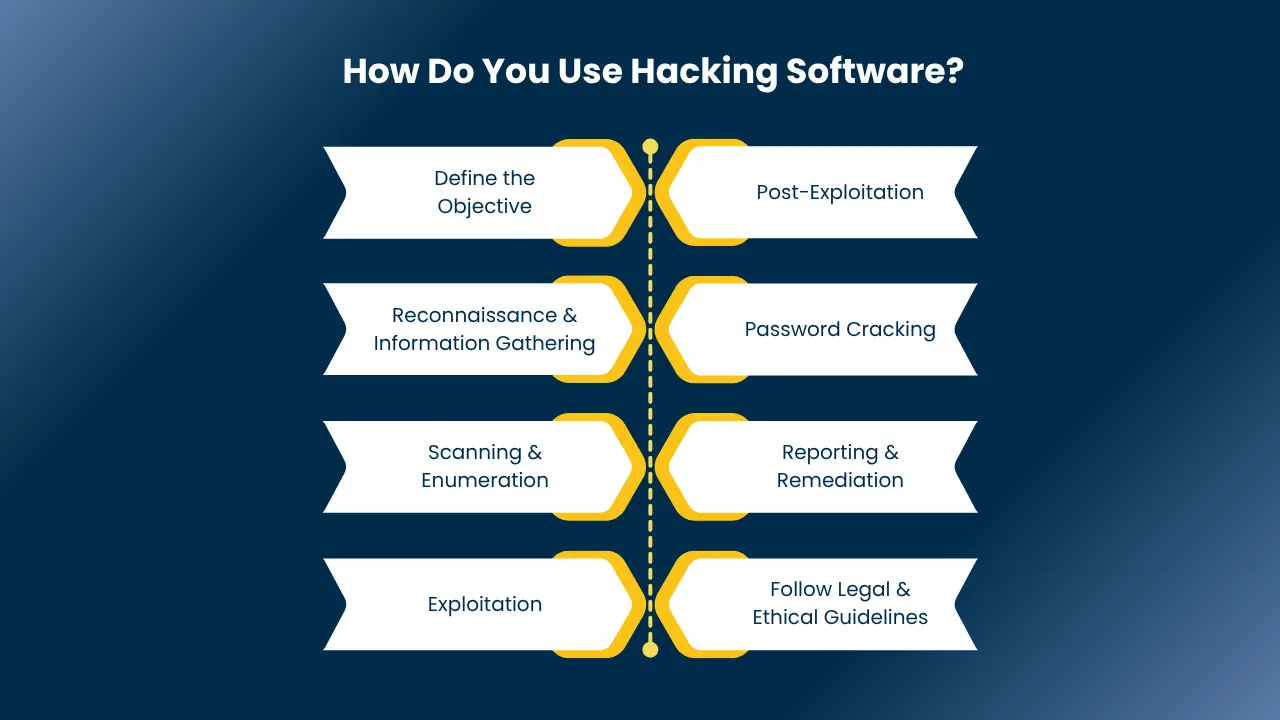
How Do You Use Hacking Software?
Hacking software is designed to help ethical hackers simulate cyberattacks and assess system vulnerabilities. To use such software effectively and legally you must follow structured methodologies and ethical guidelines. Below is a step-by-step overview of how professionals use hacking software in real-world scenarios:
1. Define the Objective
Before launching any tool, clearly define the goal of your engagement:
- Are you conducting a vulnerability assessment, penetration test, or red team simulation?
- Are you targeting a network, web application, or IoT device?
2. Reconnaissance & Information Gathering
Start with OSINT (Open Source Intelligence) tools like:
- Maltego, Shodan, theHarvester: These tools help gather information about the target such as domain names, IP ranges, open ports, emails, and more.
3. Scanning & Enumeration
Next, use tools like:
- Nmap, Nessus, OpenVAS: These scanning tools in ethical hacking detect open ports, services, and potential vulnerabilities in the system.
4. Exploitation
Once vulnerabilities are identified, ethical hackers use exploitation tools to simulate attacks:
- Metasploit, SQLMap, BeEF: These tools allow execution of payloads to test for privilege escalation, remote code execution, or database vulnerabilities.
5. Post-Exploitation
After gaining access, analyze how much control you have:
- Mimikatz, Empire, CrackMapExec: These tools help extract credentials, pivot laterally, or maintain persistence.
6. Password Cracking (if needed)
Recover or crack user credentials using:
- Hashcat, John the Ripper, Hydra: Often used to test password strength policies.
7. Reporting & Remediation
Document your findings and recommend fixes:
- Highlight exploited vulnerabilities
- Suggest secure configurations
- Share logs and screenshots
8. Follow Legal & Ethical Guidelines
Only use hacking tools on systems you own or are authorized to test. Always work within the legal boundaries and maintain full documentation for accountability.
Is Using Hacking Tools Legal?
Yes, when used ethically and with permission. Ethical hackers (white-hat hackers) legally use these tools to identify vulnerabilities and strengthen security always within authorized boundaries.
Organizations hire ethical hackers for penetration testing, red teaming, and vulnerability assessments. These activities are not only legal but essential for cybersecurity.
Read More: How to Become Security Engineer after doing Pent Certification
Master the Top Hacking Tools and AI Tools with Cybersec Trainings
The cybersecurity landscape is advancing fast and so are the tools used by professionals. From reconnaissance and password cracking to AI-driven threat detection, mastering these tools is no longer optional for aspiring ethical hackers it’s essential.
At Orbus Cybersec Trainings, our flagship Certified Ethical Hacker (CEH) program is designed to give you practical, hands-on experience with the industry’s top 100 hacking and AI tools. You won’t just learn about tools like Metasploit, Burp Suite, or Hashcat in theory you’ll use them in simulated environments that mirror real-world attacks.
Our CEH course puts a strong focus on:
- Practical tool usage in real-life penetration testing scenarios
- Understanding how hackers think and how to defend against them
- Integrating modern AI tools like ThreatGPT and Microsoft Security Copilot in incident response
- Learning to automate tasks using platforms like Recon-ng, SpiderFoot, and AutoSploit
Whether you’re just starting out or looking to upskill, our curriculum is built to keep you ahead of evolving threats. With expert instructors, project-based learning, and continuous mentoring, you’ll gain the confidence to operate in red team environments and respond effectively to real-world security challenges.
Conclusion
Mastering the right ethical hacking tools is critical for any cybersecurity professional in 2025. From reconnaissance to exploitation and AI-driven detection, each tool featured in this list offers unique advantages for identifying and mitigating security risks. However, tools alone aren’t enough proper training and application are key. That’s where Orbus Cybersec Trainings comes in. Through hands-on CEH courses and expert guidance, you’ll learn not just to use these tools but to think like a hacker and defend like a pro. Ready to elevate your ethical hacking skills? Join us today.