So, you’re a penetration testing master with your CPENT certification. You’re discovering vulnerabilities, hacking your mind, and hardening systems. But where’s the next step? If you want to advance your career and move into a leadership position, becoming an Information Security Manager may be the right path for you. It’s a step that combines technical skill with strategic planning, and it’s one that’s closer to reach than you may believe. This blog will take you through the process, illustrating how your CPENT skills can be the springboard to a successful information security management career. We’ll examine the role, the career path, and transitioning, so you’re prepared to make the next big step.
Role of an Information Security Manager
An Information Security Manager (ISM) is the core individual in the cybersecurity operations of an organization. Their primary duty is to protect sensitive information and systems from threat and maintain regulation compliance.
- Policy Development: Developing and putting into practice security policies and processes.
- Risk Management: Discovering, evaluating, and reducing security threats.
- Security Training: Providing employees with training on security best practices.
- Incident Response: Coordinating and managing incident responses to security breaches.
- Compliance Management: Making sure that there is compliance with industry standards and legal mandates.
- Technology Oversight: Maintaining the installation and upkeep of security technologies.
- Team Leadership: Supervising and commanding security staff.
- Stakeholder Communication: Being the focal point for security issues.
- Budget Management: Managing resources to fund security projects.
- Continuous Improvement: Keeping abreast of new threats and technology.
Essentially, an ISM is responsible for the overall security posture of an organization, combining technical expertise with managerial skills to protect critical assets.
How CPENT Certification Helps in Becoming an Information Security Manager
The CPENT certification isn’t just a technical badge; it’s a solid stepping stone towards an Information Security Manager role. It bridges the gap between hands-on testing and strategic security management.
1. Solid Technical Foundation
CPENT offers in-depth, hands-on penetration testing expertise. This enables you to comprehend vulnerabilities from the bottom up, essential for developing successful security programs.
2. Practical Relevance
The hands-on approach of CPENT, as highlighted by Orbus Cybersec Trainings, ensures you’re ready for real-world security issues. You’ll be able to implement your knowledge in real-world situations.
3. Industry Acceptance
CPENT is an accepted credential, confirming your skills and improving your employability with employers.
4. Vulnerability Awareness
You must be aware of your penetration testing companies security position as an ISM. CPENT provides you with the capability to detect and analyze vulnerabilities, a central part of security planning.
5. Good Communication
You will be able to convey technical results in understandable, actionable reports, which are vital for communicating with stakeholders.
6. Strategic Prioritization
CPENT trains you to prioritize vulnerabilities and create mitigation strategies, a skill that should be a staple of every good manager.
7. Current Expertise
Keeping up with threats is essential. CPENT familiarizes you with the newest penetration testing methods, so you are always one step ahead of new cyberattacks.
8. Developing Security Programs
The CPENT experience lets you understand how to construct robust security programs, as you will already know the ways in which systems can be compromised.
Essentially, CPENT is offering the experiential, real-world education that directly maps over to an Information Security Manager’s strategic mindset.
Career Path and Job Opportunities
So, you’re eyeing becoming an Information Security Manager? That’s a good one. It’s a job where you get to design and oversee security plans, work with a team, and keep everything in line. It’s a challenge, but it’s worth it.
- Starting Out: You’ll probably start with jobs such as IT support, network administration, or even security analyst. This is where you get your hands dirty and learn the foundation.
- Moving Up: You can move up to a Senior Security Analyst or an IT Project Manager. You’ll be handling risk management, incident response, and getting more into cybersecurity protocols.
- Reaching the Manager Level: This is when you become an Information Security Manager. You’ll be writing security policies, conducting vulnerability assessments, and managing your team.
- The Top Tier: After a while, you might end up in executive positions such as IT Director, Chief Technology Officer (CTO), or even Chief Information Officer (CIO).
Let’s discuss the type of jobs you’ll encounter along the way:
- Security Analyst: Those who monitor the systems, seeking trouble.
- Penetration Tester (Ethical Hacker): Those who attempt to breach systems to identify vulnerabilities. (CPENT certification indicates you mean business with this!)
- Security Engineer: The security system builders and maintainers.
- Security Architect: The secure network designers.
- Security Consultant: The cybersecurity strategy advisors.
- Chief Information Security Officer (CISO): The head of security.
- Information Security Manager: Your desired role, overseeing overall security.
- Cybersecurity Manager: Manages network and computer security.
- IT Auditor: Verifies that security controls are functioning.
- Incident Responder: Manages security breaches.
- SOC Manager: Operates the security operations center.
- Data Security Manager: Guards sensitive data.
- Cloud Security Manager: Protects cloud environments.
- Cybersecurity Specialist: Specializes in a specific security domain.
- Security Administrator: Manages security systems.
- Security Trainer: Trains employees.
- Security Researcher: Explores new threats.
- Security Program Manager: Creates security programs.
- Security Compliance Officer: Manages compliance.
- Security Risk Manager: Identifies security risks.
In general, there are all sorts of roles in cybersecurity, and CPENT can help get you into many of them, particularly ones that can progress to a management role.
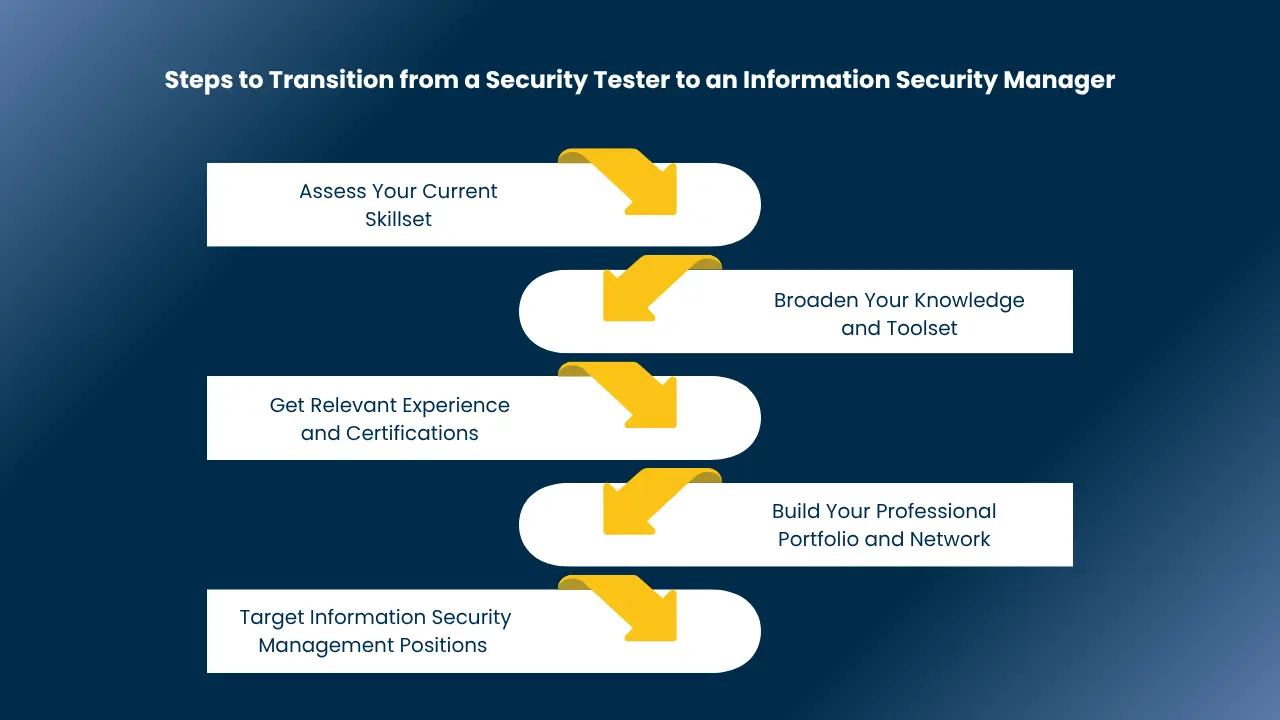
Steps to Transition from a Security Tester to an Information Security Manager
Transcending from security testing to information security management is a natural career move. You have the technical hands-on skills; now it’s time to develop the strategic and leadership skills. Here’s a step-by-step guide on how to make that transition:
1. Assess Your Current Skillset
- Sincerely review your expertise in penetration testing, vulnerability scanning, and other testing disciplines.
- Determine gaps. Do you know risk management, compliance, or incident response?
- Don’t overlook soft skills: communication, problem-solving, and teamwork are essential to management.
2. Broaden Your Knowledge and Toolset
- Cybersecurity is in constant flux. Stay current on new threats and technology.
- Learn about topics outside testing: risk management, security governance, and compliance.
- Take online penetration testing courses, read industry publications, and attend webinars to acquire knowledge.
3. Get Relevant Experience and Certifications
- Look for chances to use your skills in wider security scenarios.
- Look at industry-recognized penetration testing certifications (such as those provided by Orbus Cybersec Trainings) that prove your skills. CPENT is a good place to begin.
- Volunteer for projects or apply for entry-level security jobs to gain more experience.
4. Build Your Professional Portfolio and Network
- Display your work in a portfolio: reports, findings, and any projects you’ve completed.
- Network with other penetration testing cyber security professionals. Go to industry events, participate in online forums, and establish relationships.
- Social media sites such as LinkedIn are extremely helpful for networking.
5. Target Information Security Management Positions
- Research the requirements of Information Security Manager jobs.
- Customize your resume and cover letter to emphasize your applicable skills and experience.
- Practice for interviews: anticipate technical, behavioral, and strategic interview questions.
Basically, you are expanding on the technical knowledge you already possess, and then adding layers of management and strategic thinking.
Conclusion
The transition from a security tester to an Information Security Manager is one that demands technical competence as well as strategic thinking. Your certified information security manager certification is a solid foundation, equipping you with the hands-on experience required to comprehend and counter vulnerabilities. By broadening your knowledge, acquiring relevant experience, and developing your professional network, you can move into a management position with confidence. Remember, the field of cybersecurity is ever-changing, so endless learning and adaptation are essential. Join the challenge, harness your CPENT skills, and you’ll be halfway to achieving a rewarding career as an Information Security Manager and protecting your organization’s digital assets.